Protective Security Case Study
Remit
The remit of this case study demonstrates how social listening can be leveraged to enhance the security of key individuals and sites. Monitoring vast quantities of data can assist law enforcement, government agencies or private enterprises in bolstering their capacity to detect threats and protect assets of interest.
The Topic
This case study will focus on insights extracted from a threat monitoring framework that KINSHIP Digital constructed at the request of a client. Social listening was conducted across open-source domains and social media platforms for a period of 11 months.
Purpose
This case study was conducted to achieve two key outcomes:
Demonstrate how social listening platforms can be used to improve individual and site security through the detection of threats.
Present how the analysis of threat data and hostile narratives can be used to inform security operations and risk analysis.
Background
An organisation was responsible for the protection of multiple individuals and locations within Australia that were assessed to be at an increased risk of harm. While this organisation possessed a sophisticated physical security capability, its ability to identify threats proactively across social media remained limited and resource-intensive- often relying on the manual analysis of online discussions to detect threats.
This presented a significant security risk, whereby potential threats were unable to be detected and subsequently actioned due to the volume and breadth of the digital information landscape. This was further compounded by the approach of a heightened period of operations for the organisation after an anticipated increase in threat volume.
The Challenge
The growth, accessibility and reach of social media and the internet more broadly provide an additional operating environment for law enforcement and intelligence organisations. Contemporary instances of violence against individuals or groups have often been preceded by either statements of explicit intent to carry out such actions or suggestive language that indicated so. These digital clues are therefore a central part of proactive threat detection, which is crucial to maintaining security operations that are both efficient and comprehensive.
While manual methods of online threat detection may have initially been suitable, the rapid growth of the information landscape, which has grown by 23.13% in 2025 alone, renders such methods obsolete. This is validated by the steady increase of internet access in both developing and developed nations (98% of Australia’s population now has access to the internet), coupled with the widespread adoption of social media, with 78% of Australians active on social channels in 2025. Even with a large and well-trained group of analysts, it is impossible to keep pace with this growing data landscape. Social listening, therefore, becomes a necessity to capture unstructured data at scale and extract relevant, actionable information.
The Application
This case study utilised targeted social listening and placed a number of individuals in need of protection at its centre. Data was collected from a predefined date range between 2024 and 2025 and was configured to detect harmful messages across two different languages.
Discussions that contained both harmful content and a reference to these individuals were surfaced automatically. This included both responses to posts from these people in question, as well as separate independent discussions. These messages would then be subsequently triaged for action and prioritised according to threat intensity.
Unpacking Threat Data
Analysis of threat data revealed clear periods of threat frequency and intensity, as well as dormancy. At the conclusion of the monitoring period, the following data was collected:
Direct Threats
Across the monitored personnel, 29 messages were categorised as direct threats following their detection. Primarily, these messages contained a direct and clear intention to cause harm. The volume of such messages increased during heightened periods of online discourse and sensitivity and were often clustered rather than sporadic.
Messages detected by the monitoring framework and subsequently classified as direct threats.
Vague Threats
Less direct threats were detected in higher quantities, either alluding to an intent to commit violent acts or expressing a desire for violence to occur. 59 messages were classified into this category.
Messages identified and classified as vague threats.
Narrative Reinforcement
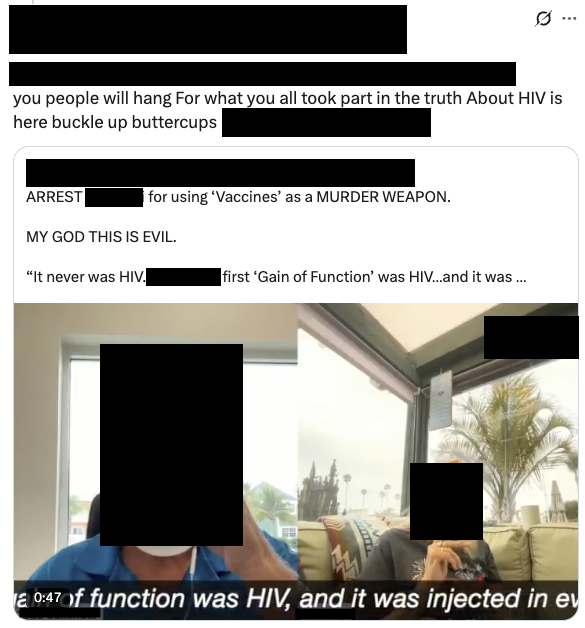
Detected messages also served to provide insights into prevalent narratives surrounding key individuals. Their significance, based off the frequency in which such content was detected within harmful messages, can subsequently assist in the formation of tailored threat monitoring frameworks and prioritisation of counternarratives.
One of multiple posts which perpetuated anti-vaccination narratives in relation to the persons of interest monitored. Such narratives are key to understanding the momentum of possible threats to wider social cohesion in addition to specific individuals.
Mapping Threat Language
Threats online can not only be understood by their volume but also by the way they are expressed and interconnected. In this case study, the three layers of threat expression that were observed can assist in the identification of risk trends, such as periods of increased threat activity, key themes driving hostile discourse, and potential escalation pathways, showing how vague or indirect messaging can evolve into direct threats. Understanding these connections enables security teams to prioritise responses, anticipate flashpoints, and inform risk analysis more effectively.
Conclusion
This case study demonstrates how social listening can be leveraged as an operational force multiplier for protective security, permitting the extraction of threats effectively across online spaces that would otherwise prove un-navigable via conventional scanning. The ability to automatically surface threat language, classify intent, and map hostile narratives closed a critical gap in the client’s security posture, enabling earlier visibility of emerging risks that would otherwise remain undetected.
Beyond individual threat detection, narrative insights provided context around why threats were escalating, enabling security teams to prioritise resources, adjust posture before risk peaks, and inform strategic mitigation decisions.
In doing so, this approach shifted social media monitoring from reactive manual scanning to proactive threat intelligence, creating a repeatable model for organisations seeking to strengthen protective operations at scale.